This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Nowcomm - Now Powered by FourNet
We are proud to say that Nowcomm is now part of FourNet. One of Cisco’s top partners, Nowcomm brings to FourNet a wealth of specialist skills and expertise which will enable us to provide a significantly enhanced cybersecurity, networking and collaboration offering to our customers.

Cybersecurity and Collaboration Experts
In an increasingly digital landscape, cybersecurity and online safety are top priorities for many organisations. In our interconnected world, the importance of safeguarding your sensitive information cannot be overstated. Our expert team of cybersecurity professionals provides the highest level of defence against ever-evolving threats. With our cutting-edge technologies and proactive approach, we offer a range of solutions tailored to meet your specific needs. Rest easy knowing that our UK-based team is at the forefront of the cybersecurity environment, constantly monitoring and adapting to emerging risks. Discover peace of mind and take control of your digital life with our comprehensive cybersecurity services.
Threat Assessment and Prevention
In the ever-evolving world of cybersecurity threats, proactive measures are crucial to safeguarding your digital assets. At FourNet, our Threat Assessment and Prevention services provide you with a robust defence against potential risks. Our team of skilled cybersecurity experts conducts comprehensive assessments to identify vulnerabilities in your systems, networks, and applications.
With state-of-the-art tools and methodologies, we meticulously analyse potential attack vectors, emerging threats, and weak points in your infrastructure. Armed with this valuable intelligence, we implement tailored prevention strategies to mitigate risks and fortify your defences. By staying one step ahead of cybercriminals, we ensure that your sensitive data and critical information remain safe from unauthorised access, data breaches, and other malicious activities.

Explore Cyber Security From FourNet
7 Step Secure Plan
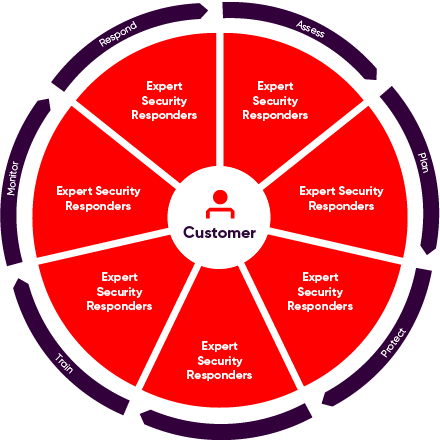
Access
Expose your cyber security weaknesses, understand where you are at risk and see the path forward.
Plan
Develop a comprehensive and actionable cyber incident plan.
Protect
Keep your employees safe no matter where and how they work.
Defend
Managed Detection & Response
Train
For proactive organisation-wide security awareness.
Monitor
Discovery and prevention of compromised credentials on the Dark Web.
Cyber Incident Response
Mitigate damages, improve cybersecurity, and maintain stakeholders' trust.
Customer Success Stories



Forewarned is Forearmed
Every company is vulnerable. With an attack every 11 seconds globally, your organisation is likely to fall victim of cyber criminals at some point.
However, you can take action right now by preparing for this eventuality. It is in your company’s best interests to have a well thought out cyber incident plan.
Our Secure Plan can assist you in developing a comprehensive and actionable cyber incident plan that will help you quickly restore operations, minimise losses, fix vulnerabilities and thoroughly strengthen security to avoid future incidents.
Employee Awareness Training
We know your employees are an integral part of your cybersecurity defence strategy. That’s why we offer comprehensive Employee Awareness Training to equip your staff with the knowledge and skills necessary to identify and respond to potential threats effectively. Our expert trainers deliver engaging and interactive sessions that cover a wide range of cybersecurity topics, including phishing attacks, social engineering, password security, and safe browsing practices.
By educating your employees on best practices and the latest trends in cyber threats, we empower them to become the first line of defence against potential breaches. Our training programs are tailored to your specific industry and organisational needs, ensuring that your workforce remains vigilant and capable of mitigating risks. Invest in your team’s cybersecurity awareness today and strengthen your overall security posture with FourNet.

Compliance and Regulatory Support
Navigating the complex landscape of cybersecurity compliance and regulations can be daunting. That’s why at FourNet, we offer comprehensive Compliance and Regulatory Support to ensure your organisation remains aligned with the latest industry standards.
Our team of experienced professionals is well-versed in the intricacies of data protection laws and regulations, such as GDPR, PCI DSS, HIPAA, and more. We provide thorough assessments of your current practices, policies, and procedures to identify any gaps or areas of non-compliance.
With our guidance, we help you implement robust measures to meet regulatory requirements and mitigate the risk of penalties or legal issues. Our tailored solutions are designed to align your cybersecurity practices with the specific regulations relevant to your industry, providing you with peace of mind and a solid foundation for maintaining a secure environment. Stay ahead of compliance challenges and let FourNet be your trusted partner in achieving regulatory excellence.
Security Quick Guides
Effective cyber security requires a focused and layered approach to be successful.
It’s often difficult to determine precisely how much of a threat you are up against and what you should do about it. We’ve written these guides to help you understand how to ensure your organisation’s security works for you.
Our guides focus on risks, challenges, trends, and potential impacts and outline actionable steps to mitigate them.